HTTPD server also knows as Apache2 server is a very commonly used server in many production environments. It is tested and trusted. This server has many usages and you can extend its functionality by installing modules like mod_proxy, proxy_connect, proxy_balancer and the list goes on. In this blog post I'll be showing how to use HTTPD server as a load balancer with minimum number of configuration steps.
Install and Prepare the HTTPD server
If you are using a Linux Debian distribution such as Ubuntu or Linux mint, you can simply install it by issuing the following command.- apt-get install apache2
Once the server is successfully installed you need to install mod_proxy related modules. In order to do that execute the following command.
- aptitude install -y libapache2-mod-proxy-html libxml2-dev
Now you just need to enable proxy_module, proxy_balancer_module and proxy_http_module. It can be done by executing the following command.
- a2enmod proxy
- a2enmod proxy_balancer
- a2enmod proxy_http
To verify if the modules are installed and enabled properly, use the following command.
- apache2ctl -M | grep proxy
Configuring the cluster
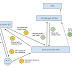
Following is the cluster setup we will be configuring.
Basically, what we are going to have is two WSO2 ESBs fronted by the HTTPD server. As you may have already noticed, I have used port offset 1 for ESB -1 and port offset 2 for ESB -2. You can change the port of each ESB by configuring below element of <ESB_HOME>/repository/conf/carbon.xml.
<!-- Ports offset. This entry will set the value of the ports defined below to the define value + Offset. e.g. Offset=2 and HTTPS port=9443 will set the effective HTTPS port to 9445 --> <Offset>1</Offset>
Likewise you can change the port offset to 2 for ESB -2 as well. Apart from these for testing purposes I have deployed the below Proxy service in each ESB.
OK 1
Now that you have configured two WSO2 ESBs, let's look at how we can configure HTTPD server. It is very easy. Open the default configuration file for HTTP and add following configuration. The default configuration file is 000-default and it can be found under /etc/apache2/sites-enabled/
Just before the end of VirtualHost section you need to add the following two entries.
ProxyPass /httpd/ balancer://mycluster/
ProxyPassReverse /httpd/ balancer://mycluster/
Once that is done add the following configuration at the very top of (even before the VirtualHost section) 000-default file.
<Proxy balancer://mycluster>
# Define back-end servers:
# Server 1
BalancerMember http://localhost:8281/
# Server 2
BalancerMember http://localhost:8282/
</Proxy>
Just before the end of VirtualHost section you need to add the following two entries.
ProxyPass /httpd/ balancer://mycluster/
ProxyPassReverse /httpd/ balancer://mycluster/
Once that is done add the following configuration at the very top of (even before the VirtualHost section) 000-default file.
<Proxy balancer://mycluster>
# Define back-end servers:
# Server 1
BalancerMember http://localhost:8281/
# Server 2
BalancerMember http://localhost:8282/
</Proxy>
Now save the file and restart HTTPD server. This can done by executing the following command.
After restarting the server start the two WSO2 ESBs. Once the servers are started use the following request to see if the cluster is working.
- sudo service apache2 restart
- curl -v http://localhost/httpd/services/MyMockProxy
[2015-03-15 16:03:54,073] INFO - LogMediator To: , MessageID: urn:uuid:4a6e90ae-de16-4828-b416-176250a269d9, Direction: response, HIT = HIT
Yep, It is that easy to load balance WSO2 ESBs with HTTPD server. To learn more about HTTPD server you can refer to the below links.
[1] https://www.digitalocean.com/community/tutorials/how-to-use-apache-http-server-as-reverse-proxy-using-mod_proxy-extension
[2] http://httpd.apache.org/docs/2.2/mod/mod_proxy.html
[3] http://wiki.centos.org/HowTos/Https
[4] http://httpd.apache.org/docs/2.2/mod/mod_proxy_balancer.html
.png)
.png)






.png)
